The Definitive Guide to Private Stablecoin Payments
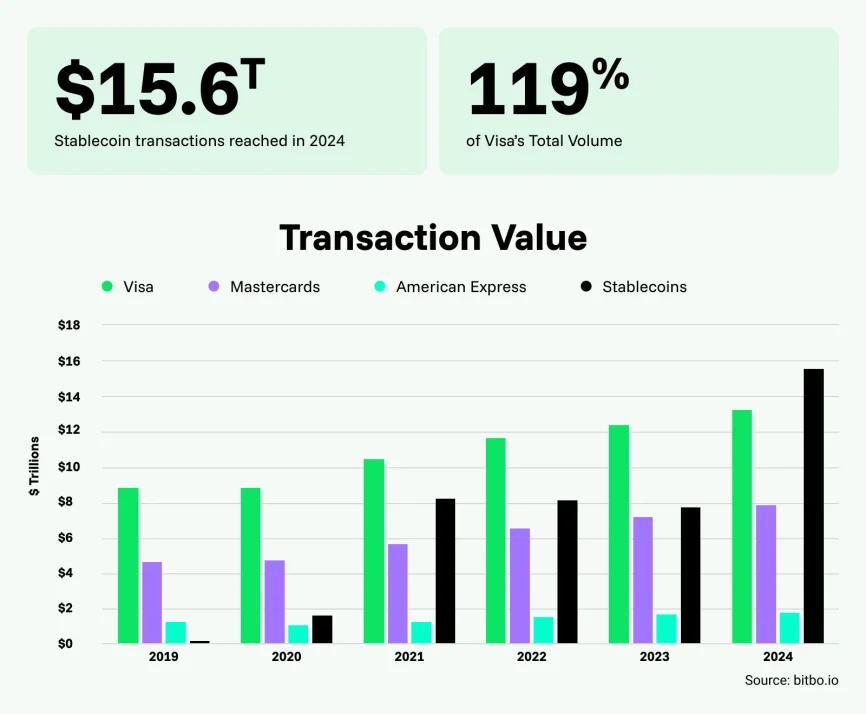
Stablecoins have emerged as a powerful tool for global commerce, promising instant, borderless, and low-cost transactions. Stablecoins are reshaping global commerce, with on-chain volume processing over $8.9 trillion in the first half of 2025 alone. But for merchants, especially those in high-risk sectors, a critical and often overlooked issue lurks beneath the surface: privacy.
The public nature of most blockchains exposes sensitive business data, creating significant commercial risks. This article serves as the definitive guide for merchants on how private stablecoin payments work, the technologies that make them possible, and how to implement a payment strategy that delivers both security and sovereignty.
The Privacy Paradox: Why Standard Stablecoin Payments Aren’t Private
This section explains that public blockchains offer pseudonymity rather than true anonymity, creating a paradox where transaction transparency, intended for security, exposes sensitive commercial data and creates significant business risks.
Public blockchains like Ethereum (ETH) have revolutionized digital payments, but they operate on a principle of radical transparency that creates a significant privacy paradox for businesses. Many believe that crypto transactions are anonymous, but the reality is that they are merely pseudonymous. This fundamental misunderstanding can turn a company's financial data from a private asset into a public liability.
On a public blockchain, every transaction detail—the sender's wallet address, the receiver's address, the amount, and the timestamp—is permanently recorded and visible to anyone. While real-world identities aren't directly tied to these alphanumeric addresses, the entire financial history of a wallet is open to public scrutiny and blockchain analysis, making privacy not just a preference, but a core operational necessity for any serious on-chain payments guide.
As Vitalik Buterin, co-founder of Ethereum, notes, "Crypto is not just about trading tokens, it's part of a broader ethos of protecting freedom and privacy and keeping power in the hands of the little guy".
This paradox forces businesses to rethink their data strategy, especially when dealing with sensitive industries like iGaming or adult entertainment.
Are crypto payments anonymous? The Illusion of Anonymity on Public Blockchains
This section clarifies that most crypto payments are pseudonymous, not anonymous, because while real names are hidden, all transaction data on a public ledger can be tracked and potentially linked back to real-world identities through on-chain analysis.
No, most crypto payments on public blockchains are not anonymous; they are pseudonymous, and the distinction is critical for any business operating in the Web3 space. Pseudonymity means that while your real name isn't attached to your wallet address, your entire transaction history is. Every payment you send or receive is a permanent entry on a public ledger.
Specialized firms and savvy competitors can use on-chain analysis tools to trace the flow of funds, link your on-chain activity to off-chain data (like a known exchange account), and ultimately de-anonymize your business operations. This makes it possible for anyone to track your revenue, payment frequency, and customer interactions, creating a level of exposure that is unthinkable in traditional finance. This is why many businesses seek out an anonymous crypto payment processors to protect their operations.
Commercial Risks of Radical Transparency for Merchants
This section outlines the specific commercial dangers merchants face from the complete transparency of public blockchains, including competitive espionage, targeting by malicious actors, privacy violations, and increased regulatory scrutiny.
For legitimate businesses, particularly those in competitive or high-risk sectors like iGaming and adult entertainment, this level of public exposure presents several critical risks. The radical transparency of standard crypto payments can undermine a company's competitive edge and expose it to significant threats.
- Competitive Disadvantage: Competitors can perform on-chain analysis to reverse-engineer your financial health. They can monitor transaction volumes to estimate revenue, identify key suppliers by tracking payments, and analyze customer payment patterns to inform their own strategies.
- Targeting by Malicious Actors: A publicly visible wallet with a high balance is a prime target for hackers and scammers. By observing transaction flows, malicious actors can identify high-value targets and tailor phishing attacks or other exploits to compromise your assets.
- Customer and Employee Privacy Violations: For businesses in sensitive industries, the public nature of transactions can inadvertently expose customer payment habits. Similarly, using stablecoins for payroll on a public blockchain can reveal confidential salary information, creating security and privacy risks for employees.
- Regulatory Scrutiny: High-volume or unusual transaction patterns on a public ledger can attract unwanted attention from regulatory bodies. This is a core challenge for any high-risk merchant trying to operate legitimately.
How Do Private Stablecoin Payments Work? The Architectural Blueprint
This section explains that private stablecoin payments work by introducing a "privacy layer" that separates the confidential details of a transaction from the public act of its verification on the main blockchain.
To solve the privacy deficiencies of public blockchains, a new architecture for digital payments has emerged that fundamentally re-engineers how crypto payments work. The key is a conceptual shift from a single, public event to a two-step process involving a privacy layer. Instead of broadcasting all transaction details to the public ledger, the sensitive data—who paid whom and how much—is handled off-chain or in an encrypted state. What is submitted to the main public ledger, like Ethereum, is merely a cryptographic guarantee, or proof, that a valid transaction occurred according to the network's rules. The public ledger's role is reduced to that of a verifier and settlement layer; it confirms a valid transaction happened, but it doesn't learn the confidential details. This decoupling of a transaction's execution from its verification is the cornerstone of on-chain privacy, often enabled by Layer-2 solutions and Zero-Knowledge Proofs (ZKPs).
According to a report from the Bank for International Settlements, "regulatory responses to global stablecoins should take into account the potential of other stablecoin uses, such as embedding a robust monetary instrument into digital environments, especially in the context of decentralised systems".
With Layer-2 adoption trending high and transaction counts more than doubling on major L2s after Ethereum's Dencun upgrade, this architectural shift is rapidly becoming the new standard.
The Three Pillars of On-Chain Privacy
This section breaks down on-chain privacy into three core technological pillars: confidentiality of identity (who), confidentiality of amount (how much), and verifiability (proof of validity).
This privacy-preserving architecture is supported by three core technological pillars, each designed to conceal a different aspect of a transaction while maintaining cryptographic integrity.
- Confidentiality of Identity: This pillar focuses on hiding the "who"—the sender and receiver of the funds. Advanced techniques like stealth addresses, which are one-time-use addresses generated for each transaction, prevent the linking of payments to the same recipient, breaking the chain of traceability.
- Confidentiality of Amount: This pillar conceals the "how much"—the value/asset type being sent. This is achieved through cryptographic commitments, a technique that allows a party to commit to a value while keeping it hidden, enabling the network to perform mathematical operations to verify integrity without ever decrypting the underlying amounts.
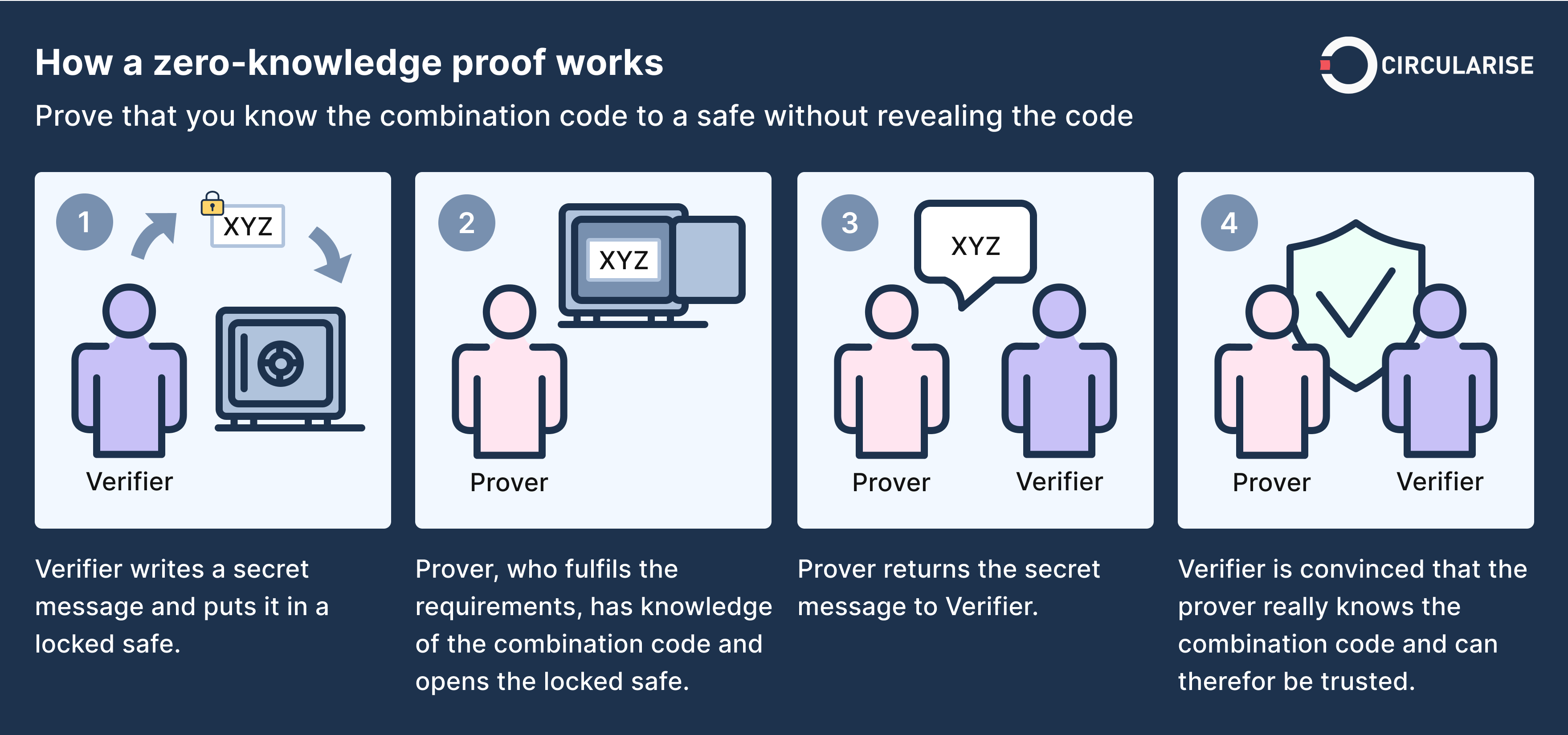
- Verifiability: This is the most critical pillar, ensuring that privacy does not come at the cost of security. The network must be able to confirm that a transaction is valid—for instance, that the sender has sufficient funds—without accessing the confidential data. This is accomplished through Zero-Knowledge Proofs (ZKPs), which allow a party to prove a statement is true without revealing any of the information that makes it true.
Core Technologies Enabling On-Chain Privacy: A Merchant's Guide
This section provides merchants with an accessible guide to the four primary technologies that enable on-chain privacy: Zero-Knowledge Proofs (ZKPs), Confidential Transactions (CTs), Layer-2 solutions, and crypto mixers.
Achieving private stablecoin payments requires a sophisticated toolkit of cryptographic techniques and blockchain architectures. For merchants, understanding these core technologies is essential for selecting a payment solution that offers robust privacy without compromising security or scalability. Here is a breakdown of the primary technologies that enable on-chain confidentiality.
As noted by McKinsey, "Choosing issuance and transaction of stablecoins on low-latency Layer 1 and 2 blockchains (scaling solutions to improve processing speeds) reinforces their value proposition as a lower-cost alternative".
This is especially true as Layer 2 stablecoin transactions have increased by 54% year-over-year, demonstrating a clear market shift toward more efficient and private infrastructure.
Zero-Knowledge Proofs (ZKPs): Proving Without Showing
This section explains that Zero-Knowledge Proofs (ZKPs) are cryptographic protocols that allow a transaction's validity to be proven to the blockchain without revealing any of the sensitive data within it, such as the sender, receiver, or amount.
A Zero-Knowledge Proof (ZKP) is a cryptographic protocol where one party (the prover) can prove to another (the verifier) that a statement is true, without revealing any information beyond the validity of the statement itself. An intuitive analogy is the "Ali Baba cave," where a person proves they know a secret password to open a magic door inside a circular cave without the verifier ever learning the password. In stablecoin payments, ZKPs generate a proof confirming all network rules were followed (e.g., sufficient funds), but do so without revealing transaction details to the public blockchain. The two main types are zk-SNARKs, which are small and fast but require a trusted setup, and zk-STARKs, which are larger and more transparent without a trusted setup.
Confidential Transactions (CTs): Hiding the Numbers
This section describes how Confidential Transactions (CTs) use cryptographic techniques like Pedersen Commitments and homomorphic encryption to encrypt transaction amounts and asset types while still allowing the network to verify the ledger's integrity.
Confidential Transactions (CTs) are a set of cryptographic techniques focused on encrypting transaction amounts and asset types while still allowing the network to verify the integrity of the ledger. The core technology is the Pedersen Commitment, a form of homomorphic encryption that allows computations to be performed on encrypted data. A commitment is created that "blinds" the transaction amount, and because of the homomorphic property, the network can confirm that the sum of committed inputs equals the sum of committed outputs without ever knowing the actual values. To further enhance identity privacy, CTs can be combined with Ring Signatures, a technique used by privacy coins like Monero to group a sender's transaction with others, making it computationally infeasible to determine the true sender.

Privacy-Centric Layer-2 Solutions: The Execution Environment
This section explains that Layer-2 solutions, particularly ZK-Rollups, provide the scalable infrastructure needed to execute a high volume of private transactions off-chain before settling them efficiently on the main blockchain.
While ZKPs and CTs provide the cryptographic foundation for privacy, Layer-2 (L2) solutions provide the practical infrastructure for deploying them at scale. L2s are protocols built on top of a main blockchain (like Ethereum) that handle transactions off-chain to increase speed and reduce costs, while still relying on the L1 for security. ZK-Rollups are a type of L2 perfectly suited for private payments. They work by "rolling up" hundreds of private transactions off-chain, generating a single ZKP for the entire batch, and submitting only that compact proof to the L1 mainnet for verification. This drastically reduces data on the main chain, leading to significant scalability gains and lower fees while preserving the confidentiality of each transaction. Privacy-focused L2s like Aztec, Fhenix, and Celo are designed specifically for this purpose.

Crypto Mixers: The Double-Edged Sword of Anonymity
This section defines crypto mixers as services that obscure transaction trails but warns merchants about the extreme regulatory risk, citing the sanctioning of Tornado Cash by OFAC as a key reason to avoid them for legitimate business.
Crypto mixers, or tumblers, are services that enhance anonymity by breaking the on-chain link between a sender and a receiver. They achieve this by pooling funds from many users and shuffling them before sending them to their final destinations, making it difficult to trace the original source. However, for legitimate businesses, mixers represent a significant and often unacceptable risk. Regulators view them with extreme suspicion due to their widespread use in money laundering, and prominent mixers like Tornado Cash have been sanctioned by government bodies such as the U.S. Office of Foreign Assets Control (OFAC). Interacting with a mixer can lead to a business's funds being flagged, a key issue covered in the definitive guide to tainted funds. This highlights the shift from the "unstructured anonymity" of mixers to the "structured confidentiality" offered by modern ZKPs, which can balance privacy with compliance.
A Practical Workflow: From Customer Checkout to Private Settlement
This section illustrates a real-world, step-by-step workflow of a private stablecoin payment for an iGaming platform, from the initial customer checkout to the final, private settlement in the merchant's self-hosted wallet.
To understand how these technologies come together, consider the workflow for a private stablecoin payment at an online iGaming platform—an industry where both payment speed and customer privacy are paramount. A recent case study showed that by integrating stablecoin rails, a gaming startup achieved a 90% reduction in payment latency and a 35% higher conversion on in-game purchases. This process shows how a transaction can be settled instantly and confidentially using a modern, self-hosted crypto payment gateway.
According to one industry expert, "For gaming operators, stablecoins deliver the best of both worlds: the speed and borderless efficiency of crypto rails with the predictability of fiat. That's why stablecoins are increasingly becoming the default for cross-border payments, deposits, and payouts in gaming".
- Customer Checkout: A player on the iGaming site decides to deposit 100 Tether (USDT) to their account. At checkout, the merchant's self-hosted payment gateway generates a unique payment request.
- The Privacy Layer in Action: The player's crypto wallet interacts with a ZK-Rollup. The transaction details (sender, receiver, amount) are encrypted on the player's device, and a zero-knowledge proof is generated attesting to the transaction's validity without revealing the encrypted data.
- On-Chain Verification: The encrypted data and the ZKP are submitted to the ZK-Rollup's smart contract on the Ethereum mainnet. The L2 operator bundles this with hundreds of other private transactions into a single batch, generates one consolidated ZKP for the entire batch, and posts only that compact proof to Ethereum for verification.
- Private Settlement: Once the L2 block is finalized on Ethereum, the 100 USDC is credited to the iGaming platform's self-hosted wallet on the L2 network. Only the merchant can decrypt and view their updated balance. Settlement occurs in seconds, a critical advantage in iGaming.
- Off-Ramping with Control: With the funds settled in their self-custodied wallet, the merchant has complete control. They can hold the stablecoins, use them for instant payouts, or convert them to fiat through a compliant off-ramp service.
The Compliance Tightrope: Balancing Privacy with AML/KYC Obligations
This section addresses the critical question of regulatory compliance, explaining how a "compliance by design" model using zkKYC and verifiable credentials can satisfy AML/KYC requirements without compromising user privacy.
For any legitimate business, adopting privacy-enhancing technologies raises a critical question: how can one maintain confidentiality while adhering to strict Anti-Money Laundering (AML) and Know-Your-Customer (KYC) regulations? The regulatory landscape is evolving, with initiatives like the EU’s MiCA (Markets in Crypto-Assets), FATF (Travel Rule) and the The GENIUS Act in the US mandating robust AML/KYC programs for stablecoin issuers.
The solution lies not in weaker privacy, but in smarter, "compliance-by-design" systems. As explored by institutions like the IMF, this model uses ZKPs to create a system that is both private and compliant. Users first verify their identity with a licensed third party to enter a "KYC perimeter." They are then issued a cryptographic verifiable credential, which is used to generate a zkKYC token—a ZKP that proves the user is KYC-verified without revealing their identity on-chain. Smart contracts can then monitor for high-risk activity and, if necessary, trigger a lawful disclosure process, balancing commercial confidentiality with regulatory obligations.
As Caroline Pham, Acting Chairman of the CFTC, stated, "You cannot have innovation without having a safety-first approach. It's not a trade-off, it goes together".
This approach is critical, especially as Chainalysis estimates that $25 billion to $32 billion in stablecoins were received by illicit actors in 2024.
Strategic Implementation: Choosing the Right Privacy Model for Your Business
This section provides a strategic framework for merchants, comparing custodial versus self-hosted gateways and permissioned versus public blockchains, and ultimately recommending a "sovereign composability" model for maximum control and resilience.
Implementing a private stablecoin payment solution is not a one-size-fits-all endeavor. Merchants, especially those in high-risk industries, must make strategic choices about their payment architecture to balance privacy, control, and compliance. The key decisions revolve around the custody model of the payment gateway and the type of blockchain network used for settlement. The strong search interest in terms like self hosted crypto payment gateway is clear evidence of a market desire for this financial sovereignty.
Gil Penchina, Former CEO of Wikia Inc., highlights the merchant's perspective: "For merchants, it is an amazing opportunity. Compared to Paypal, crypto has no credit card fees, no charge backs, no 'Oops, we decided to hold your cash for 3-12 months while we investigate something we can't disclose'".
This sentiment is echoed in countless online discussions where merchants share stories of having their accounts frozen by traditional processors.
Custodial vs. Self-Hosted (Non-Custodial) Gateways: The Control Dilemma
This section contrasts third-party custodial payment solutions like Stripe with self-hosted gateways, highlighting the critical risk of de-platforming for high-risk merchants and the financial sovereignty offered by non-custodial options.
The first major decision is whether to use a custodial or a self-hosted payment gateway. Custodial solutions, like those offered by Stripe, manage wallets and funds on behalf of the merchant, offering simplicity at the cost of control. For businesses in high-risk sectors, this model is precarious, as the provider can freeze funds or terminate the account at any time. In contrast, a self-hosted (non-custodial) solution means the merchant runs the software on their own servers, giving them exclusive control over their private keys and funds. This approach is the foundation of an unbannable gateway architecture, as it eliminates the risk of being de-platformed by a payment processor.
Permissioned vs. Public Blockchains: The Ecosystem Trade-Off
This section compares the closed, controlled environment of permissioned networks like the Canton Network with the open and liquid ecosystem of public blockchains that utilize privacy layers like ZK-Rollups.
The second strategic choice concerns the underlying blockchain network. Permissioned blockchains, such as the Canton Network, are private networks where only authorized participants can validate transactions. They offer a controlled environment that can simplify compliance but create a siloed ecosystem with limited market access. The alternative is to use a public, permissionless blockchain like Ethereum but conduct transactions on a privacy-focused Layer-2 solution like a ZK-Rollup. This model provides access to the vast liquidity and user base of the broader public blockchain ecosystem while still enabling confidential transactions. For merchants seeking resilience, it offers greater decentralization and avoids being locked into a single, proprietary network.
Implementation Blueprint: Your Guide to Financial Sovereignty
This section provides a straightforward, step-by-step guide for transitioning to a self-hosted payment system.
Step 1: Setting Up Your Secure Wallet
The foundation of your crypto payment system is a secure, non-custodial wallet where you, and only you, control the private keys to your funds.
First, secure a hardware wallet, such as a Ledger or Trezor. This is the digital equivalent of a physical vault it stores your private keys offline, making them immune to online hacking. For daily operations, a "hot wallet" (software-based) is necessary to interact with the payment server.
PayRam includes a built-in wallet that can be securely paired with your hardware wallet, offering an optimal blend of security and convenience. During setup, you will generate a "seed phrase" (12 or 24 words). It is absolutely imperative to write this phrase down and store it in multiple secure, offline locations. This is the master key to all your funds learn more about seed phrases and hd wallets.
Step 2: Deploying Your PayRam Instance
Follow these simplified steps to deploy your own PayRam instance, which will act as your personal, censorship-proof payment processor, ready to integrate with your website or platform.
Getting your own sovereign payment gateway running is easier than you think. While it involves setting up a server, the process is designed to be straightforward, and once deployed, all the powerful configuration is handled through PayRam’s clean, intuitive user interface—no deep technical expertise required.
- Prepare Your Server: First, you'll need a foundation for your gateway. This is typically a Virtual Private Server (VPS) from a provider like DigitalOcean or AWS. The minimum requirements are modest: a server running Ubuntu 22.04 with at least 4 CPU cores, 4 GB of RAM, and 50 GB of SSD storage. You'll also need to ensure standard web ports (80, 443, etc.) are open.
- Run the Simple Setup: With your server ready, you'll run a setup script that uses Docker to install the entire PayRam stack. This single step deploys everything you need—the core API, the database, and all necessary services—in an isolated, secure environment. For detailed commands, our Documentation has you covered.
- Configure Your Gateway in the Dashboard: Once the installation is complete, you'll access your PayRam dashboard through your web browser. This is where the magic happens. Through a simple UI, you will:
- Onboard Your Configuration: Set up your admin account and primary settings.
- Connect Your Blockchain Nodes: Go to Settings > Integrations > Node Details to connect to the networks you want to support, like Ethereum, Tron (TRX), and Bitcoin (BTC).
- Set Up Your Wallets: Navigate to the Wallet Management tab to connect the wallets where you'll receive your funds. You must add and deploy a wallet for each blockchain you plan to accept payments on.
- Onboard Your Configuration: Set up your admin account and primary settings.
- Integrate with Your Website: With your gateway configured, the final step is to connect it to your business. PayRam offers numerous simple integration options, like easy-to-embed HTML payment buttons allowing for seamless transactions.
Conclusion: The Path to Financial Sovereignty
The promise of stablecoins can only be fully realized when their privacy shortcomings are addressed. As we've seen, the public nature of blockchains like Ethereum creates tangible risks for merchants, transforming sensitive financial data into a public liability. However, a new generation of privacy-enhancing technologies—from Zero-Knowledge Proofs and Confidential Transactions to privacy-centric Layer-2 solutions—provides the tools to build a truly confidential payment architecture.
For businesses, especially those in high-risk industries, the path forward is not to retreat from this innovation but to embrace it strategically. By combining a self-hosted payment gateway with the power of ZK-Rollups on a public blockchain, merchants can achieve "sovereign composability"—a state of complete control over their funds and operations without sacrificing access to the global, liquid world of decentralized finance. This isn't just about accepting a new form of payment; it's about building a resilient, private, and future-proof financial stack.
Frequently Asked Questions (FAQ)
What are private stablecoin payments?
Private stablecoin payments are transactions made with stablecoins (cryptocurrencies pegged to a stable asset like the US dollar) that use privacy-enhancing technologies to conceal sensitive details like the sender, receiver, and transaction amount from the public blockchain.
Why aren't regular crypto payments on public blockchains private?
Regular crypto payments are pseudonymous, not anonymous. While your real name isn't attached to your wallet, every transaction is permanently recorded on a public ledger. This allows anyone to trace your entire financial history through blockchain analysis, creating significant privacy and commercial risks.
What are the main technologies behind private stablecoin payments?
The core technologies include Zero-Knowledge Proofs (ZKPs), which verify transactions without revealing data; Confidential Transactions (CTs), which encrypt transaction amounts; and privacy-centric Layer-2 solutions like ZK-Rollups, which process these private transactions efficiently off-chain.
What is a ZK-Rollup and how does it help with privacy?
A ZK-Rollup is a Layer-2 scaling solution that bundles hundreds of private transactions together off-chain and generates a single cryptographic proof (a ZKP) to validate them. This proof is then posted to the main blockchain, confirming the transactions' validity without revealing any of the confidential details contained within the batch.
Are private stablecoin payments compliant with AML/KYC regulations?
Yes, they can be. Modern systems are being built with "compliance by design," using technologies like zkKYC. This allows users to prove they have been verified (KYC) without revealing their personal identity on-chain, balancing the need for regulatory compliance with user privacy.
What's the difference between a custodial and a self-hosted payment gateway?
A custodial gateway is a third-party service that manages your private keys and funds, which is simpler but introduces the risk of being de-platformed. A self-hosted (or non-custodial) gateway runs on your own server, giving you full control over your keys and funds, which is ideal for high-risk businesses seeking financial sovereignty.
Why are crypto mixers risky for businesses?
Crypto mixers are viewed with extreme suspicion by regulators due to their heavy use in money laundering and illicit finance. Using a mixer can "taint" a business's funds, leading to them being blacklisted by exchanges and other regulated financial entities. Prominent mixers like Tornado Cash have been sanctioned by government bodies like OFAC.
What is the best payment setup for a high-risk business?
For maximum resilience and control, the ideal setup for a high-risk business combines a self-hosted payment gateway with privacy-enhancing technologies like ZK-Rollups that settle on a public Layer-2 blockchain. This provides financial sovereignty, commercial privacy, and access to global liquidity.
Ready to take control of your payments? Discover how one of the best crypto payment gateways can provide the privacy, security, and sovereignty your business needs.
Contact our experts today for a private consultation.


.svg)









.svg)